KTern
IP Engine | Physical and Server Security
The
cloud data centers in which the KTern IP Engine is managed feature a layered
security model, including safeguards like custom-designed electronic access
cards, alarms, vehicle access barriers, perimeter fencing, metal detectors, and
biometrics. The data center floor features laser beam intrusion detection. The
data centers are monitored 24/7 by high-resolution interior and exterior
cameras that can detect and track intruders. Access logs, activity records, and
camera footage are reviewed in case an incident occurs. Data centers are also
routinely patrolled by experienced security guards who have undergone rigorous
background checks and training.
Homogeneity,
combined with ownership of the entire stack of servers, greatly reduces the
security footprint and allows to react to threats faster. The verification of
the system firmware and software components is also ensured in the hyperclouds, and
it establishes a strong, hardware-rooted system identity.
KTern
IP Engine | API Security
All
IP related services of KTern are managed through a secured global API gateway
infrastructure. This API-serving infrastructure is only accessible over
encrypted SSL/TLS channels, and every request must include a time-limited
authentication token generated via human login or private key-based secrets
through the authentication system described above. All platform API requests
are logged and
services are secured through HTTPS protocol and always encrypt customer content
that is stored at rest.
Encryption
is automatic, and no customer action is required. One or more encryption
mechanisms are used. For example, any new data stored in persistent disks is
encrypted under the 256-bit Advanced Encryption Standard (AES-256), and each
encryption key is itself encrypted with a regularly rotated set of master keys.
Cloud Interconnect and managed VPN allow you to create encrypted channels
between your private IP environment on premises and KTern IP Engine hosted hypercloud
network.
The hypercloud’s
intrusion detection involves tightly controlling the size and make-up of attack
surface through preventative measures, employing intelligent detection controls
at data entry points, and employing technologies that automatically remedy
certain dangerous situations. It identifies the most common vulnerabilities,
specifically cross-site scripting (XSS) and mixed content, in the web
applications. KTern managed hypercloud’s
state-of-the-art security and privacy features can help our customers secure
genetic data and support compliance with applicable data privacy/protection
regulations.
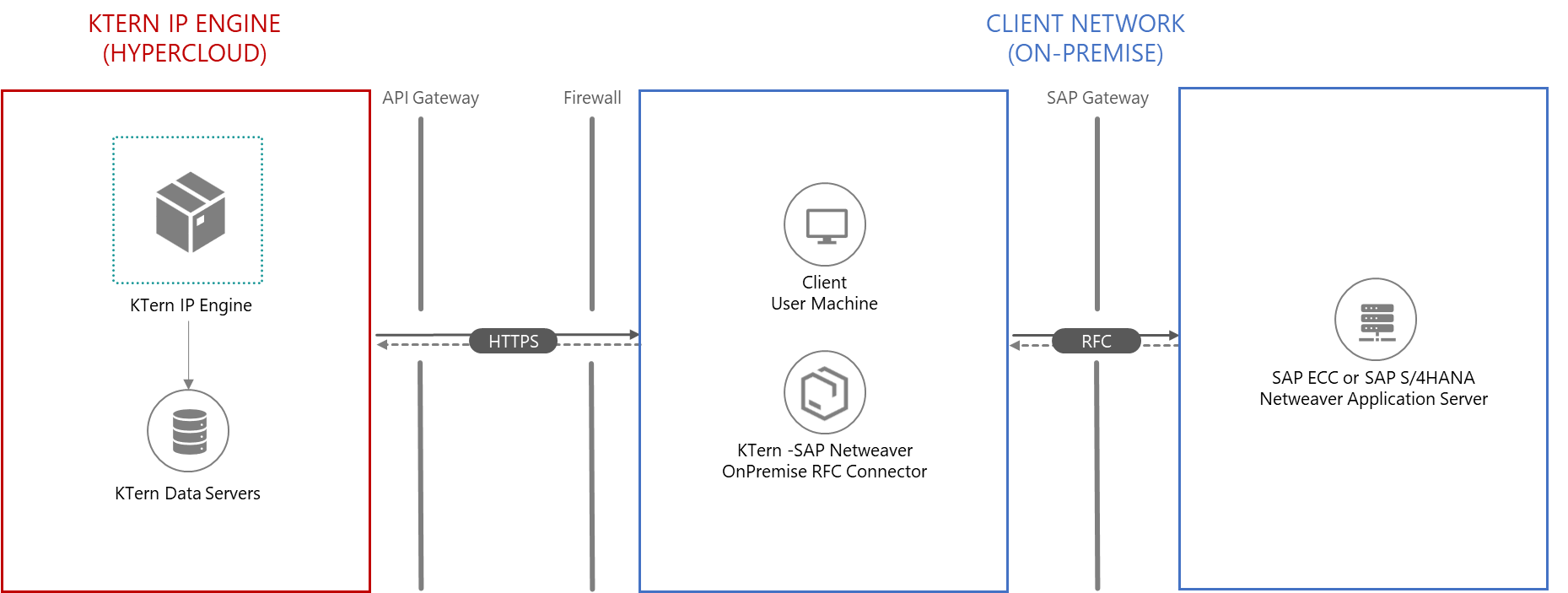
KTern
| On-Premise RFC Communication
KTern’s
automated capabilities are utilized for S/4HANA transition project, thanks to
the communication between KTern – SAP Netweaver RFC
Connector and SAP Netweaver
Application Server by means of standard RFC protocol. To perform respective
automation items, KTern's IP
Engine in hypercloud
requires certain data from on-premise ECC system extracted through RFC function
modules, only for analysis and strictly not for storing the data. It
combines an easy-to-use standard business APIs provided by SAP with
unprecedented performance for KTern's
analysis, processing using KTern's
S4HANAPEDIA and to finally store only the processed results in its cloud
database.
The
RFC communication is achieved through the secured SAP gateway via 33xx port,
where xx is the instance number of the corresponding SAP ERP / SAP S/4HANA
system. As the integration is viewed in terms of technical interoperability,
the enablement of application users and the client IT team is ensured for
better transparency and viability in the overall process of KTern On-Premise
RFC communication.
KTern
IP Engine | Data Access and Disposal
The hyperclouds in
which KTern IP engine is managed, the controls and practices are established to
protect the security of KTern IP information. The layers of the application and
storage stack require that requests coming from other components are
authenticated and authorized. Access by KTern production application
administrative engineers to production environments is also controlled. A
centralized group and role management system is used to define and control
engineers’ access to production services, using a security protocol that
authenticates engineers using short-lived personal public key certificates;
issuance of personal certificates is in turn guarded by two-factor
authentication.
When
an account is deleted, all associated data is destroyed within 50 business days
with prior notification to the account stakeholders. KTern also offers data
export options which businesses can use if they want a backup of their data
before deletion.